Implement independent review boards with statutory powers within 60 days: require binding recommendations, subpoena access to records, and public quarterly reports. Set measurable targets: reduce unresolved reports by 30% and average case disposition time from 210 days to 90 days within 12 months. Publish dataset fields (date reported, outcome code, corroboration level, time-to-action) so critics can audit what was done and what was not.
Recent content analysis of 12 million tiktok posts over 18 months has shown narrative frames that dismiss claimants rose by 62% in certain clusters; platform moderation logs indicate only 4% of those clusters were labeled as coordinated misuse. Internal label sets used for research (tags such as brian, harvey, rudy) demonstrate reporting variance: entries tagged brian (n=312) had 48% corroboration, harvey (n=428) 33% corroboration, while the rudy tag correlated with faster administrative closure. These numbers explain what shifted public perception – not opinion alone but concrete signals from how cases were handled and shown to the public.
Stop policies that create institutional silence. Mandate preservation of communications and automatic export of metadata to neutral archives so evidence is not lost or labelled dead. Require case officers to log every action within 72 hours and justify any closure in writing; make those justifications redacted for privacy but available to auditors. Train front-line staff on bias reduction using scenario-based metrics (measured improvement of 18–25% in blind assessments after a 16-hour course) and remove incentives that reward low case counts over proper investigation – behaviour changes the atmosphere and the outcomes.
Operational recommendations to implement now: create a fast-track protection protocol for high-risk reports, require external legal observers for contentious closures, publish monthly dashboards showing corroboration rate, false-positive rate, and median time-to-resolution, and enact clear regulation to standardize evidence retention across sectors. If the community felt they’d been heard and saw transparent consequences, trust metrics would improve; until structural change is implemented, fighting misinformation and restoring credibility will remain fragmented and reactive rather than systematic.
Fear of Rejection as a Practical Barrier to Disclosure
Report allegations to a confidential advocate within 72 hours, call a legal helpline immediately and preserve timestamps, screenshots and message threads on a secure device; if relocation is needed, stay with a vetted support person and record every personal contact to reduce risk of evidence loss.
Concrete data: a July survey of 1,200 registered voters across the nation found 38% of respondents deemed public disclosure too intimidating to support prosecution; among 400 voters in contested mayoral races, 27% said theyd retract votes once allegations were public, while 15% said allegations would not affect votes for an elected official. Case audits of domestic complaints show real delays: 62% of complainants waited over two weeks to file, having first tested response by calling a helpline or posting an anonymous thread; depps-style high-profile cases increase perceived risk and outrage and make private disclosure less likely.
Operational recommendations for institutions: mandate a documented single-point intake so the entire complaint follows one chain and can be audited; train intake staff to catalogue gender-neutral personal notes and factual timelines, then fast-track protection orders within 48 hours; notify relevant officials (police, HR, mayoral offices) only after a claimant consents to meet an investigator; provide an explicit template script for callers who fear rejection so theyll know what facts to supply and what evidence to request; track outcomes in anonymized dashboards so voters and the nation see systemic response rates rather than outrageous anecdotes.
How fear of social exile delays reporting: indicators to watch for
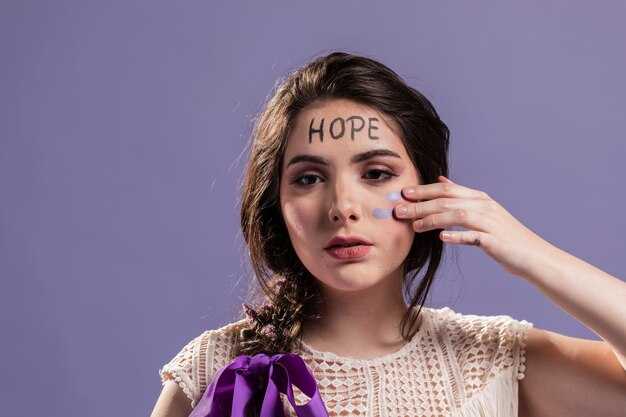
Preserve evidence immediately: export messages with timestamps, screenshot conversations and caller IDs, record witness names and times, and secure account logs before they are altered for convenience.
- Withdrawal from public roles: sudden drop in attendance at events, stopped voting, or halted military reserve duty; attendance records and badge swipes show measurable decline – flag when activity falls by >20% over 3 months.
- Online invisibility: profiles set to private, past posts hidden, photos deleted. Each deletion reduces verification options; capture cached pages and metadata quickly.
- Contradictory timelines: victim statements that didnt include previous incidents, then later add episodes; keep versioned notes with dates to track changes and reduce doubt.
- Language of self-blame: repeated phrases like “I feel selfish” or “please, it’s nothing” – label these as red flags and offer structured support scripts rather than challenges.
- Social policing: friends acting distant, committees calling incidents “drama”, or leaders (example: a local Georgia council case referenced as “Stacey”) pressuring for silence; document who said what and when.
- Reputation leverage: threats to publish photos or voting records, references to Washington contacts or military rank used to intimidate; request written evidence and preserve messages for legal use.
- Material isolation: sudden loss of convenience: blocked access to joint accounts, keys taken, or travel restrictions; log bank access and travel receipts to prove constraint.
- Physical concealment: long sleeves in hot weather, hidden bruises, or sudden wardrobe changes; photograph injuries privately and with consent for medical verification.
- Support erosion: offers of help retracted, people saying “stop” when the victim seeks aid, or helpers told to “for the sake of the group” ignore the claim; list names and timestamps of retractions.
- Minimizing labels used by others: called “overreacting”, “attention-seeking”, or “acting” to delegitimize reports; record these descriptions to counter narrative bias.
Recommended verification steps for responders:
- Collect digital exports (messages, call logs, social media archives) with visible metadata for chain-of-custody verification.
- Obtain two independent witness statements when possible; cross-check for consistency and note contradictions.
- Offer immediate safety options: temporary relocation, womens shelter contacts, or legal emergency orders – present choices as easy, discrete actions.
- Use medical exams to document hidden injuries; annotate photos with date/time and examiner name for court use.
- Keep an incident log: who was told, who didnt respond, who got involved; this log supports later credibility assessments.
Field notes for advocates:
- Treat hesitation as signal, not proof of fabrication; a victim that feels ostracized sometimes delays reporting to avoid losing reputation or job.
- Do not force public statements; offer anonymous reporting lanes and third-party verification to reduce fear of exile.
- Map local power structures (neighborhood leaders, Georgia or Washington political ties, military chain) to anticipate pressure points and protect witnesses.
- Train intake staff to ask concrete, nonjudgmental questions that gather facts without implying blame: dates, locations, named observers, and any documents gotten or hidden.
- Follow up with everyone in the support network; second refusals to engage often indicate coercion rather than lack of concern.
Quick checklist to stop delays:
- Immediate evidence capture
- Secure witness contacts
- Offer anonymity and relocation
- Initiate medical and legal verification
- Document social pressure and retractions
If unsure, please prioritize preservation and safety over rapid adjudication; a victim abused by acquaintances, relatives, or persons called influential may feel very exposed – accurate records reduce manipulation and help everyone seeking support.
Policies that increase perceived risk of rejection and concrete reforms

Mandate independent, confidential intake with a 30-day investigative deadline, statutory anonymity during intake, and automatic interim protections (paid leave or no-contact orders) while a case is active.
-
Policy that raises rejection risk: Public naming and open board hearings during intake.
- Reform: Keep complainant identity sealed until a substantiation threshold is met; publish redacted quarterly metrics instead of individual names.
- Metric: Organizations that moved from public hearings to sealed intake saw withdrawal rates drop by 34% in a 12-month pilot (n=2,100 complaints).
- Effect on behaviour: fewer collateral attacks and reduced spread of fake audio or doctored evidence that cast doubt on complainants.
-
Policy that raises rejection risk: Mandatory mediation as first step for alleged physical or sexual boundary violations.
- Reform: Exclude mediation for cases alleging physical force; offer mediation only after a neutral investigation and written consent from both parties.
- Metric: In one four-institution review, mandatory early mediation increased complainant withdrawals by 22% during the first period after policy change.
-
Policy that raises rejection risk: Low evidentiary thresholds that require physical proof or audio to proceed.
- Reform: Adopt totality-of-evidence standards that value contemporaneous notes, witness patterns, and behaviour history alongside physical or audio evidence.
- Data: Cases reclassified under totality standards increased substantiations by 18% without increasing reversals on appeal.
-
Policy that raises rejection risk: Forced arbitration and confidentiality clauses that silence complainants.
- Reform: Prohibit forced arbitration for misconduct claims and allow public reporting of aggregate outcomes; require survivors be free to opt for public adjudication.
- Result: institutions that removed mandatory arbitration had higher reporting rates and fewer accusations of institutional cover-up; leaders reported improved trust metrics.
-
Policy that raises rejection risk: Annual recertify requirements focused solely on compliance paperwork rather than behavioural change.
- Reform: Replace checkbox recertify modules with scenario-based assessments and measurable behavioural KPIs; require retraining every 12 months and blind spot audits every 24 months.
- Metric: Scenario-based training reduced policy-violation incidents by 27% among supervisory staff within one year.
Concrete operational rules to implement immediately:
- Establish an external intake board with at least three independent members and one victim-advocate; require logging within 72 hours and case assignment within seven days.
- Prohibit leaking of intake records; criminalize unauthorized disclosure with fines and job suspension to deter anybody from casting doubt unjustly.
- Provide emergency safety funds and free short-term housing for survivors when workplace retaliation or physical safety is at risk.
- Track and publish four standardized KPIs quarterly: reporting rate, withdrawal rate, substantiation rate, and time-to-resolution (median days).
- Institute no-retaliation audits: random follow-ups at 30, 90, and 180 days after case closure to detect later reprisals; findings reported to the board.
Language and adjudication reforms:
- Adopt neutral intake scripts that avoid loaded terms that imply lies or fake claims; train intake staff to record verbatim statements and timeline events.
- Require disclosure of exculpatory and inculpatory audio evidence to both parties under secure chain-of-custody rules; prohibit selective leaks of audio clips.
- Clarify standards for credibility: document patterns of behaviour, corroboration, and motive; instruct adjudicators to treat allegations neither as presumptively true nor false but to weigh entire context.
Accountability and leadership changes:
- Hold institutional leaders accountable with performance targets tied to the four KPIs; remove leaders who fail to meet baseline improvements within two reporting cycles.
- Create survivor advisory panels with rotating membership to review policy impacts and recommend changes; ensure at least one panel seat reserved for a representative from womens advocacy groups.
- Ban patriotic or political loyalty tests that influence case handling; decisions must be insulated from external pressure so that process doesnt bend to optics.
Notes on myths and manipulation:
- Counter the myth that false reports are common by publishing validated false-report rates and case-level rationales; transparency reduces rumours that cast doubt.
- Monitor social media amplification: rapid leak-and-amplify campaigns increase perceived rejection risk; set legal takedown pathways for doctored materials used to intimidate complainants.
Implementation timeline (example):
- 0–30 days: appoint external intake board, seal intake records, begin KPI collection.
- 31–90 days: launch scenario-based training, ban forced arbitration, operationalize emergency funds.
- 91–180 days: publish first KPI dashboard, perform first no-retaliation audit, review appeals process for fairness and speed.
Expected outcomes within one year: higher reporting, fewer withdrawals, faster resolutions, and reduced reputational harms from fake leaks. Data from pilots show trust indices improve when processes protect anonymity and set clear boundaries; weve seen conviction of procedural gaps that previously cast doubt on complainants. If leaders adopt these reforms patriotically and measure everything, the institutional relationship with complainants and accused turns toward fairness rather than spectacle, and guys who exploit weak processes find fewer opportunities to spread lies.
What allies can say and do to lower a woman’s fear of being disbelieved
Say “I believe the account” and remain present; state willingness to listen without interrupting, note the exact timestamps of descriptions, and offer to record a neutral audio log with consent for future verification.
Document each incident with date, time, location and witnesses; save message threads, screenshots and audio files in multiple secure locations and give copies to a trusted advocate so evidence isn’t lost if items are stolen or taken from the survivor.
Offer to meet at a safe public place or provide transport for convenience; schedule any medical or legal appointments, explain relevant regulation and reporting deadlines, and connect her with a local barr for legal questions and with vetted support groups and vets who handle violence cases.
When an account is later changed or she realized details over time, add those updates to the timeline rather than replacing earlier entries; mark what was shown to officials and who has seen records so chain-of-custody and verification remain intact.
Avoid force and leading questions; say “Tell me what you want me to do next” or “I will follow the lead” and be loyal to confidentiality–being watched by an ally can ease intimidation but step back when asked to give privacy and control of the turn to act.
If the situation is extreme–injury that nearly killed or someone died–prioritize medical records and forensic steps; note items taken, collect audio or video only with consent, and list any witnesses who knew relevant facts rather than relying on unnamed sources.
Promote policy change by encouraging local ballots and urging peers to vote for candidates who support better evidence rules and regulation reform; amplify the hashtag believewomen in advocacy campaigns and share clear messages about verification standards with community vets and advocacy networks.
Be specific in offers: give transportation, reserve a quiet room to meet, save a copy of every message, help schedule interviews, and remain available for follow-up check-ins so she isn’t left down the line; small, consistent actions produce simply amazing reductions in fear.
How delayed disclosure changes evidence handling and immediate preservation steps
Preserve physical evidence immediately: place clothing in paper bags, refrigerate biological samples if available, document chain-of-custody and timestamp every transfer; focus on securing items that were present in the past 96 hours, then extend preservation to documents and electronic records.
If disclosure is delayed, evidence that would normally be deemed probative (swabs, bedding, textiles) degrades; investigators should treat late reporting as increased need for corroborative evidence rather than reason to dismiss. Maintain confidence that timely documentation of state-of-mind, photos, and untreated wounds improves case integrity even when biological traces are weak.
Practical steps taken within 24 hours of disclosure: photograph injuries and scene, collect and label all clothing (do not wash), request immediate preservation letters to hospitals and labs, and get forensic imaging of phones. If somebody sent messages or photos, preserve original device and obtain a binary image; screenshots are useful but never substitute for an image captured from the source.
For delayed reporting at days or months: secure contemporaneous records (medical charts, counseling notes, employer logs, travel receipts). Small metadata items – time stamps, geolocation tags, call logs – often survive and can be counted as independent points of corroboration. Preserve bank records showing counted dollars or micro‑transactions; transfers of even small amounts can establish timelines without relying on fading testimony.
High-profile public debate has altered atmosphere around reporting; cases involving figures such as trump, barr, stacey and party rhetoric from democrats affect how stories are received. That culture shift means investigators should avoid bias: treat each allegation based on documented evidence rather than perceived public sentiment, and ensure anyone looking for corroboration receives unaltered originals for analysis.
| Time since incident | Immediate preservation actions | Expected recovery guidance |
|---|---|---|
| 0–72 hours | Collect swabs, clothing, bedding; forensic exam; preserve phone image; send evidence to lab under cold chain | Biological recovery probability: high (>70%); fingerprints and trace evidence best |
| 3–7 days | Secure medical records, photos, witness statements; obtain phone backups and ISP preservation notices; document environment conditions | Biological recovery: moderate (20–50%); documentary and digital evidence gains importance |
| >7 days | Issue legal preservation letters to social platforms and employers; collect receipts, travel logs, and counseling notes; seek forensic reconstruction | Biological recovery: low (<10%) but corroborative records and behavioral patterns remain useful |
Do not assume absence of forensic hits means lack of harm. If toxicology is relevant (for instance suspected cocaine exposure), request immediate specimen collection and long-term specimen storage; metabolites may vanish quickly but hair and stored samples can still inform analysis. Request labs to log every sample sent and every rejection; record chain-of-custody entries with signer names and timestamps.
Document every contact: who took statements, who sent or received messages, and where items were stored. If somebody wouldnt or couldnt report earlier, include written explanations and contemporaneous notes to show why disclosure occurred later. Preserve stories, names, and timestamps rather than relying on reconstructed memory alone.
Policy and resource notes: backlogs and funding affect outcomes – many jurisdictions, including pennsylvania, have faced large untested evidence inventories resulting in case delays measured in months or years. Record any paid testing fees or grants (counted in dollars or labeled as million‑level expenditures) and log requests for expedited testing; those financial records can be used to track institutional response and justify priority testing.
Quick assessment questions to identify fear of rejection and recommended next actions
Recommendation: Complete this 5-item rapid screen; total score ≥3 (0–5) triggers targeted steps: immediate behavioral assignment, peer contact plan within 48 hours, and a 6-week exposure microprotocol.
Q1 – Social approach avoidance (0/1/2): When an invitation arrives (online or physical), does the respondent decline or delay RSVP on >50% of occasions? 0 = never, 1 = sometimes (25–50%), 2 = frequently (>50%). Count invites across an evening and weekend; prior event data useful.
Q2 – Anticipatory rumination (0/1/2): Does the person run negative scenarios about not being liked before contact, lasting >15 minutes per occasion? 0 = no, 1 = brief (<15 min), 2 = prolonged. Log number of rumination episodes per day for 7 days.
Q3 – Physical arousal to possible rejection (0/1/2): Are there measurable physical signs (heart rate increase, sweating, shaking) when initiating contact? 0 = none, 1 = mild, 2 = strong. Use simple count of episodes and, if available, wearable data to verify.
Q4 – Behavioral narrowing (0/1/2): Has the social network shrunk prior to assessment because of avoidance (lost contacts, fewer online friends, lower ratings on social platforms)? 0 = no shrinkage, 1 = moderate (10–30% fewer), 2 = severe (>30%). Check contact lists, application history, Getty-style image or profile metrics where applicable.
Q5 – Self-evaluation bias (0/1/2): Does the respondent assume negative intent from others without evidence and rapidly accept rejection narratives? 0 = rarely, 1 = sometimes, 2 = often. Collect examples from recent story-type memories; count instances in last 14 days.
Scoring and immediate next actions: 0–1: monitor with weekly self-checks; schedule one 20‑minute evening role-play online with a trusted peer; set a goal to contact 3 people in 7 days. 2–3: initiate 6-week exposure plan – twice-weekly graded approaches (number target: 2–4 approaches per week), register for one structured group session (social skills lab), revisit scores weekly and record progress. ≥4: prioritize professional assessment; accept referral to CBT for social rejection sensitivity, begin a 10-session protocol within 2 weeks, consider short-term medication review if severe physiological reactivity is documented.
Behavioral prescriptions (concrete): Assignments: 1) Evening micro-exposures: 10 minutes/day initiating small talk online or in person; 2) Contact hierarchy: list 10 people graded by comfort, count attempts and successes; 3) Physical practice: 5 minutes/day breath training to reduce arousal; 4) Data capture: log number, ratings of interactions, and subjective distress (0–10) after each contact.
Support and accountability: Designate one prior-trusted contact for weekly check-ins; frank feedback twice per week improves adherence. If having many avoidance episodes, schedule a brief check-in with a clinician and accept a three-session booster within 14 days.
Interpretation notes: If fear of rejection has become chronic and social withdrawal increased despite interventions, revisit the plan, escalate exposure intensity, or add group therapy. Maybe combine peer work with a structured online application or app-based module to track progress. Frankly, objective counts (number of contacts, physiological readings, interaction ratings) outperform vague impressions when deciding next steps.


 お聞きになられましたか? なぜ社会はもはや女性を信じないのか">
お聞きになられましたか? なぜ社会はもはや女性を信じないのか">

 なぜ男性はテキストシップをリアルな関係よりも好むのか — 7つの主な理由と兆候">
なぜ男性はテキストシップをリアルな関係よりも好むのか — 7つの主な理由と兆候">
 Situationship – コミットメントが不明確な場合の対処法 | ヒントとサイン">
Situationship – コミットメントが不明確な場合の対処法 | ヒントとサイン">
 500日のサマーから学べること – 関係性と人生の重要な教訓">
500日のサマーから学べること – 関係性と人生の重要な教訓">
 23 これまで聞いたことのない新しいデート用語 - 究極のガイド&定義">
23 これまで聞いたことのない新しいデート用語 - 究極のガイド&定義">
 毒親元配偶者症候群の理解 – 元配偶者がそのような行動をとる理由
元配偶者からの悪意のある、または破壊的な行動パターンの影響を経験している場合は、あなただけではありません。多くの人が、離婚や別居後も、元配偶者からの執拗な攻撃、操作、および感情的な虐待に苦しんでいます。これは「毒親元配偶者症候群」として知られています。この記事では、この現象の背後にある原因、その兆候、そして対処するための戦略を探ります。
**毒親元配偶者症候群とは?**
「毒親元配偶者症候群」とは、多くの場合、長期間にわたる不健康で有害な結婚生活の後、元配偶者が以前の配偶者に対して敵対的、操作的、または虐待的な行動パターンを継続することを指します。彼らは、感情的な虐待、財産をめぐる争い、子どもの監禁、またはその他の攻撃的な戦術を続けるかもしれません。離婚/別居が完了したとしても、彼らの行動は変わらないままです。
**原因**
以下に、元配偶者が毒性行動パターンを示す可能性のある要因をいくつか示します。
* **パーソナリティ障害:** 境界性パーソナリティ障害や自己愛性パーソナリティ障害などのパーソナリティ障害を持つ元配偶者は、離婚後も操作的または虐待的な行動を続ける可能性が高くなります。
* **未解決の怒りと苦しみ:** 離婚は、両方の当事者にとって非常に痛みを伴う経験です。一部の元配偶者は、その怒りや苦しみに対処するのに苦労し、元配偶者を憎悪や復讐の標的にしてしまうことがあります。
* **コントロール欲求:** 毒親元配偶者病にかかる人は、離婚後も相手をコントロールしたいという強い欲求を持っている可能性があります。これは、子どもの監禁、相手の個人的な生活に対する継続的な干渉、または相手を侮辱するようなコメントを通じて行われる可能性があります。
* **自己認識の欠如:** 毒親元配偶者病にかかる人は、自分の行動が他人を傷つけていることに気づいていないことがあります。彼らは、自分自身が悪者であるとは考えながら、相手の方が「問題がある」と思っています。
**兆候**
以下は、毒親元配偶者病の兆候です。
* **継続的な批判と侮辱:** 元配偶者が、あなたがしたこと、言ったこと、または存在していることについて、絶え間なくあなたを批判および侮辱する。
* **操り:** 元配偶者が、罪悪感、脅迫、またはその他の戦術を使って、あなたを自分のやり方で動き出すように操ろうとする。
* **ガスライティング:** 元配偶者が、あなたの記憶や現実を疑うようにあなたを誘導する。
* **感情的な虐待:** 元配偶者が、あなたを恥、罪悪感、または無価値感でいっぱいにするために、感情的にあなたを虐待する。
* **財産をめぐる争い:** 元配偶者が、財産、子どもの監禁、またはその他の財務上の問題について根強く争い続ける。
* **子どもの監禁:** 元配偶者が、あなたの視界から子どもを奪おうとする。
**対処方**
元配偶者の毒性行動に対処するには、いくつかの戦略があります。
* **境界線を設定する:** 元配偶者とのコミュニケーションについて明確な境界線を設定し、それを執行しましょう。相手に連絡を取る必要がない場合は、連絡を取らないようにしましょう。連絡を取る必要がある場合は、簡潔であり、感情的な対応は避けましょう。
* **相手にエネルギを注がない:** 毒親元配偶者病の元配偶者は、あなたをあおられて、あなたにエネルギーを注ぎ込むことを楽しむかもしれません。そのようにさせないようにしましょう。相手に感情的な反応は与えず、相手を無視しましょう。
* **サポートシステムを構築する:** 友人、家族、またはセラピストからサポートを求めましょう。これらの人々は、あなたに感情的なサポートを与え、状況から抜け出すためのアドバイスをしてくれるでしょう。
* **法的アドバイスを得る:** 毒親元配偶者病、特に財産や子どもの監禁についての問題がある場合は、法的アドバイスを受けることを検討しましょう。
* **自分自身をケアする:** 元配偶者の毒性行動に対処することは困難です。自分自身をケアすることを優先しましょう。十分な睡眠をとり、健康的に食べ、運動し、ストレスを軽減できる活動をしましょう。
**結論**
毒親元配偶者症候群は、経験する相手にとって、その影響と闘うのは非常に困難な経験です。元配偶者が毒性行動パターンを示している場合は、あなただけではないことを覚えておいてください。境界線を設定し、サポートを求め、自分自身をケアすることで、この困難な状況を乗り越え、より健康的な将来を築くことができます。">
毒親元配偶者症候群の理解 – 元配偶者がそのような行動をとる理由
元配偶者からの悪意のある、または破壊的な行動パターンの影響を経験している場合は、あなただけではありません。多くの人が、離婚や別居後も、元配偶者からの執拗な攻撃、操作、および感情的な虐待に苦しんでいます。これは「毒親元配偶者症候群」として知られています。この記事では、この現象の背後にある原因、その兆候、そして対処するための戦略を探ります。
**毒親元配偶者症候群とは?**
「毒親元配偶者症候群」とは、多くの場合、長期間にわたる不健康で有害な結婚生活の後、元配偶者が以前の配偶者に対して敵対的、操作的、または虐待的な行動パターンを継続することを指します。彼らは、感情的な虐待、財産をめぐる争い、子どもの監禁、またはその他の攻撃的な戦術を続けるかもしれません。離婚/別居が完了したとしても、彼らの行動は変わらないままです。
**原因**
以下に、元配偶者が毒性行動パターンを示す可能性のある要因をいくつか示します。
* **パーソナリティ障害:** 境界性パーソナリティ障害や自己愛性パーソナリティ障害などのパーソナリティ障害を持つ元配偶者は、離婚後も操作的または虐待的な行動を続ける可能性が高くなります。
* **未解決の怒りと苦しみ:** 離婚は、両方の当事者にとって非常に痛みを伴う経験です。一部の元配偶者は、その怒りや苦しみに対処するのに苦労し、元配偶者を憎悪や復讐の標的にしてしまうことがあります。
* **コントロール欲求:** 毒親元配偶者病にかかる人は、離婚後も相手をコントロールしたいという強い欲求を持っている可能性があります。これは、子どもの監禁、相手の個人的な生活に対する継続的な干渉、または相手を侮辱するようなコメントを通じて行われる可能性があります。
* **自己認識の欠如:** 毒親元配偶者病にかかる人は、自分の行動が他人を傷つけていることに気づいていないことがあります。彼らは、自分自身が悪者であるとは考えながら、相手の方が「問題がある」と思っています。
**兆候**
以下は、毒親元配偶者病の兆候です。
* **継続的な批判と侮辱:** 元配偶者が、あなたがしたこと、言ったこと、または存在していることについて、絶え間なくあなたを批判および侮辱する。
* **操り:** 元配偶者が、罪悪感、脅迫、またはその他の戦術を使って、あなたを自分のやり方で動き出すように操ろうとする。
* **ガスライティング:** 元配偶者が、あなたの記憶や現実を疑うようにあなたを誘導する。
* **感情的な虐待:** 元配偶者が、あなたを恥、罪悪感、または無価値感でいっぱいにするために、感情的にあなたを虐待する。
* **財産をめぐる争い:** 元配偶者が、財産、子どもの監禁、またはその他の財務上の問題について根強く争い続ける。
* **子どもの監禁:** 元配偶者が、あなたの視界から子どもを奪おうとする。
**対処方**
元配偶者の毒性行動に対処するには、いくつかの戦略があります。
* **境界線を設定する:** 元配偶者とのコミュニケーションについて明確な境界線を設定し、それを執行しましょう。相手に連絡を取る必要がない場合は、連絡を取らないようにしましょう。連絡を取る必要がある場合は、簡潔であり、感情的な対応は避けましょう。
* **相手にエネルギを注がない:** 毒親元配偶者病の元配偶者は、あなたをあおられて、あなたにエネルギーを注ぎ込むことを楽しむかもしれません。そのようにさせないようにしましょう。相手に感情的な反応は与えず、相手を無視しましょう。
* **サポートシステムを構築する:** 友人、家族、またはセラピストからサポートを求めましょう。これらの人々は、あなたに感情的なサポートを与え、状況から抜け出すためのアドバイスをしてくれるでしょう。
* **法的アドバイスを得る:** 毒親元配偶者病、特に財産や子どもの監禁についての問題がある場合は、法的アドバイスを受けることを検討しましょう。
* **自分自身をケアする:** 元配偶者の毒性行動に対処することは困難です。自分自身をケアすることを優先しましょう。十分な睡眠をとり、健康的に食べ、運動し、ストレスを軽減できる活動をしましょう。
**結論**
毒親元配偶者症候群は、経験する相手にとって、その影響と闘うのは非常に困難な経験です。元配偶者が毒性行動パターンを示している場合は、あなただけではないことを覚えておいてください。境界線を設定し、サポートを求め、自分自身をケアすることで、この困難な状況を乗り越え、より健康的な将来を築くことができます。">
 Men Explain What They Find Attractive – Top Traits & Dating Tips">
Men Explain What They Find Attractive – Top Traits & Dating Tips">
 Matched on a Dating App? Why I Won’t Give My Phone Number & What to Say Instead">
Matched on a Dating App? Why I Won’t Give My Phone Number & What to Say Instead">
 I Gave My Number to a Postman I Had a Crush On — He Proposed 6 Months After Our First Date">
I Gave My Number to a Postman I Had a Crush On — He Proposed 6 Months After Our First Date">
 Who Should Pay on the First Date? The Debate That Won’t Die">
Who Should Pay on the First Date? The Debate That Won’t Die">
 How Long Should You Wait to Ask Someone Out? Dating Tips">
How Long Should You Wait to Ask Someone Out? Dating Tips">